Hello hacker
Two weeks ago I published my first blog post Scanning JavaScript files for Endpoints and Secrets along with a hacky bash tool and got a very good response from the community. So decided to publish another custom script of mine which is written around the legendary tool by @joohoi . This post is all about ffuf and what a beast it is. The script is written in bash and I have spent a lot of time to improvise it. So I hope it helps you in someway. Enjoy!!
A few months ago I was scrolling twitter as every hacker does, I saw that @nnwakelam is dropping some pro level tips. For those of you who don’t know, @nnwakelam is one of the million-dollar hackers and that man knows how to hack. Do give him a follow. He continuously drop some high level tips. He mentioned a tool that he thinks is a beast and was sponsoring it also.
I’m sponsoring monthly for the forseeable future https://t.co/L93FpoXITh @joohoi as what he’s built has not only made my life easier – if you get value from ffuf or other tools you use daily (especially for bounties) consider hooking your people up with some money
— n a f f y | supreme leader (@nnwakelam) October 31, 2019
But I never take anyone for his words probably due to hacker mindset and shit. So I fired up my VPS. Installed the tool and started playing with it. And oh boy!! It was a complete beast. I was getting almost 1000 requests per second on my 1 GB ram VPS.
What can you do with ffuf?
— dark_warlord14 (@dark_warlord14) January 6, 2020
1. Directory bruteforcing
2. Parameter discovery
3. Vhost bruteforcing
4. Parse waybackurls data filtered by status code, response length
It’s extremely fast. With 200 threads on 1gb ram VPS, I can get 1000 requests per second easily.#bugbountytip
I was hooked instantly. This was some incredible speed. Since then ffuf is my go-to tool. And is so flexible that you can do almost anything with it. That man @joohoi is a legend. And ffuf is his pet project. He is maintaining it quite handsomely. I am sure many have gotten bounties using only this single tool. I know at least one person who did. And that was some huge bounty.
Largest bounty was $70,000 with @hacker_ – used ffuf. pic.twitter.com/Mppyv0pQ7F
— n a f f y | supreme leader (@nnwakelam) November 5, 2019
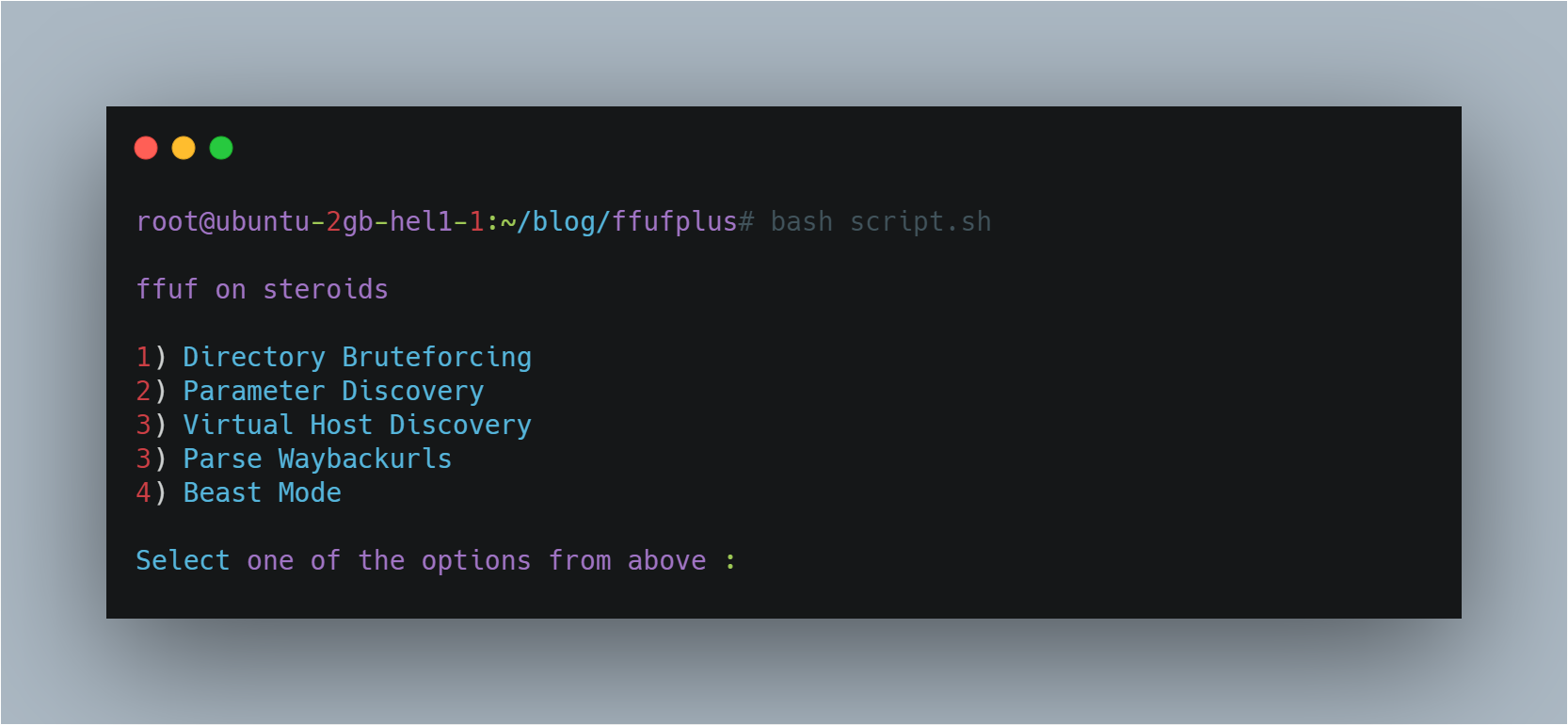
Since I was introduced to ffuf, I have been using it for many things from directory bruteforcing to parameter discovery. And it amazes me every time.I wanted to contribute to help the community in some way. So I went ahead and write this bash wrapper around ffuf which you can use to achieve
- Directory Bruteforcing
- Parameter Discovery
- VHOST Discovery
- Parse WaybackUrls
- Beast mode
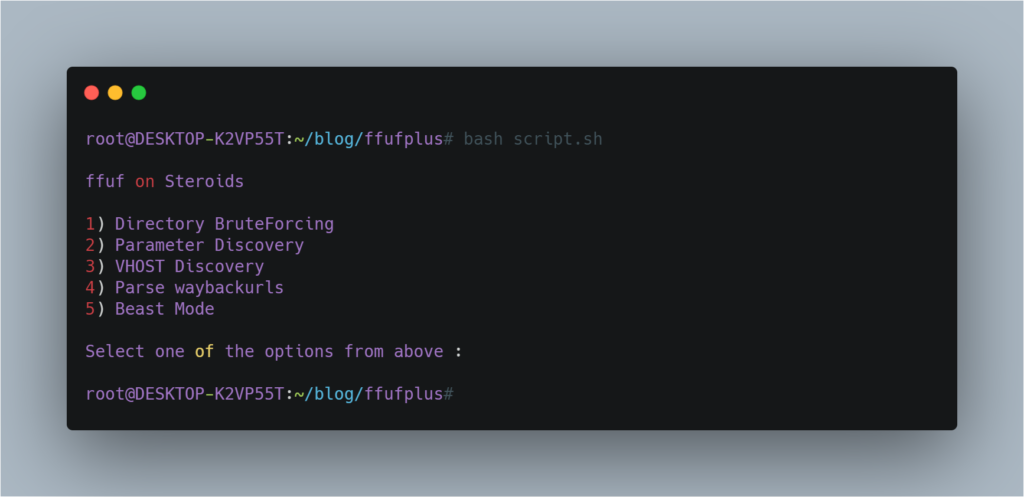
This is simple bash and pretty straightforward and this can save you a ton of time. Its very simple to use. Let me explain this options one by one
Directory Bruteforcing is simply finding endpoints on any url with default threads. This is the first step to content discovery and can yield so many interesting results if done right.
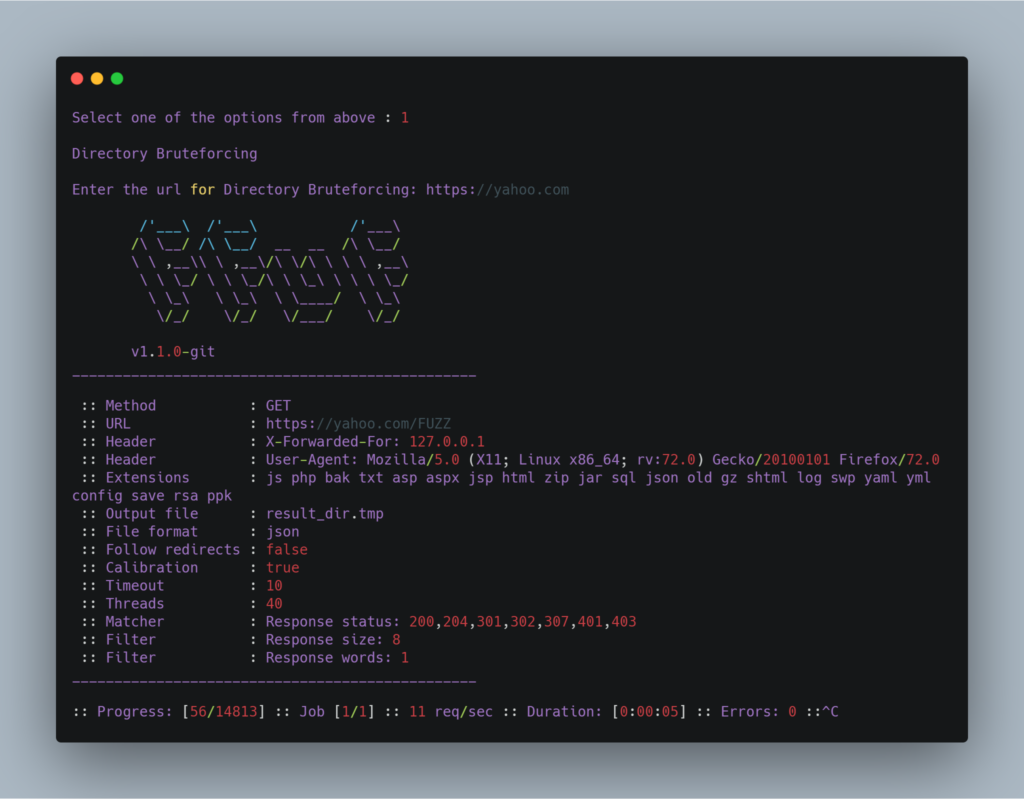
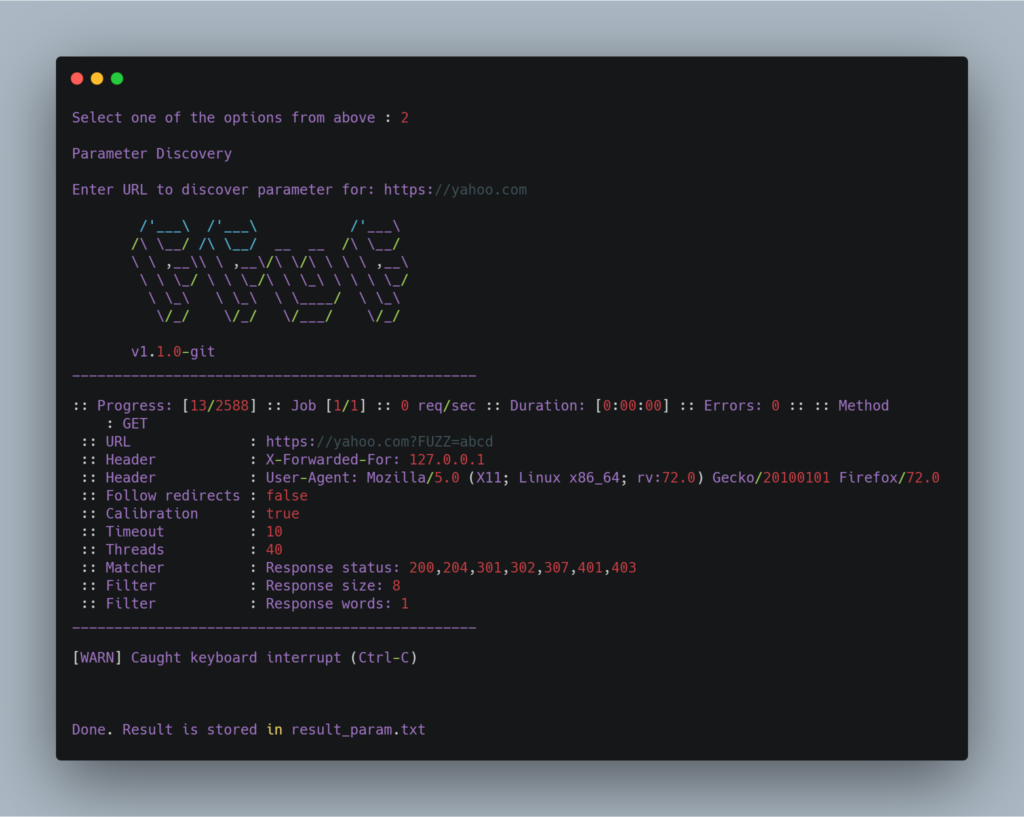
Parameter Discovery is about finding valid GET parameters for the url you want. You can then manually test those parameters for bugs like XSS, SQLI
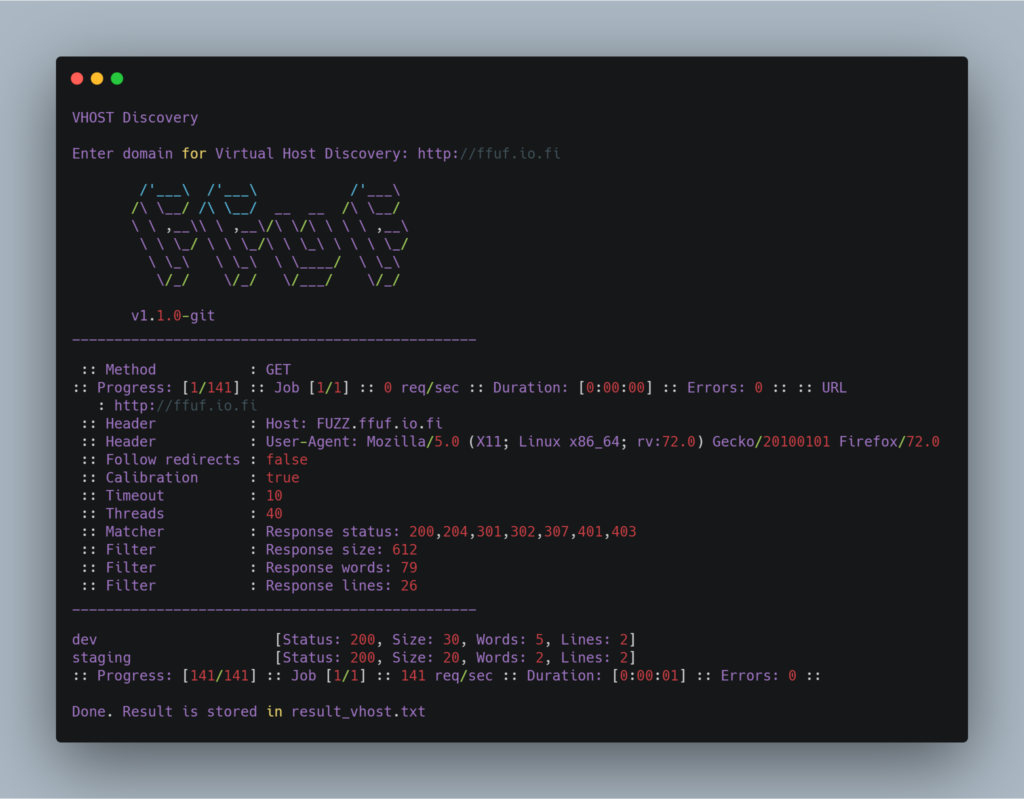
With VHOST Discovery you can discover the virtual hosts for any given domain and increase you attack surface.
Parsing Waybackurls uses gau by @hacker_ which fetch known urls from AlienVault’s Open Threat Exchange, the Wayback Machine, and Common Crawl. Then this data is parsed using ffuf to get you what you want.
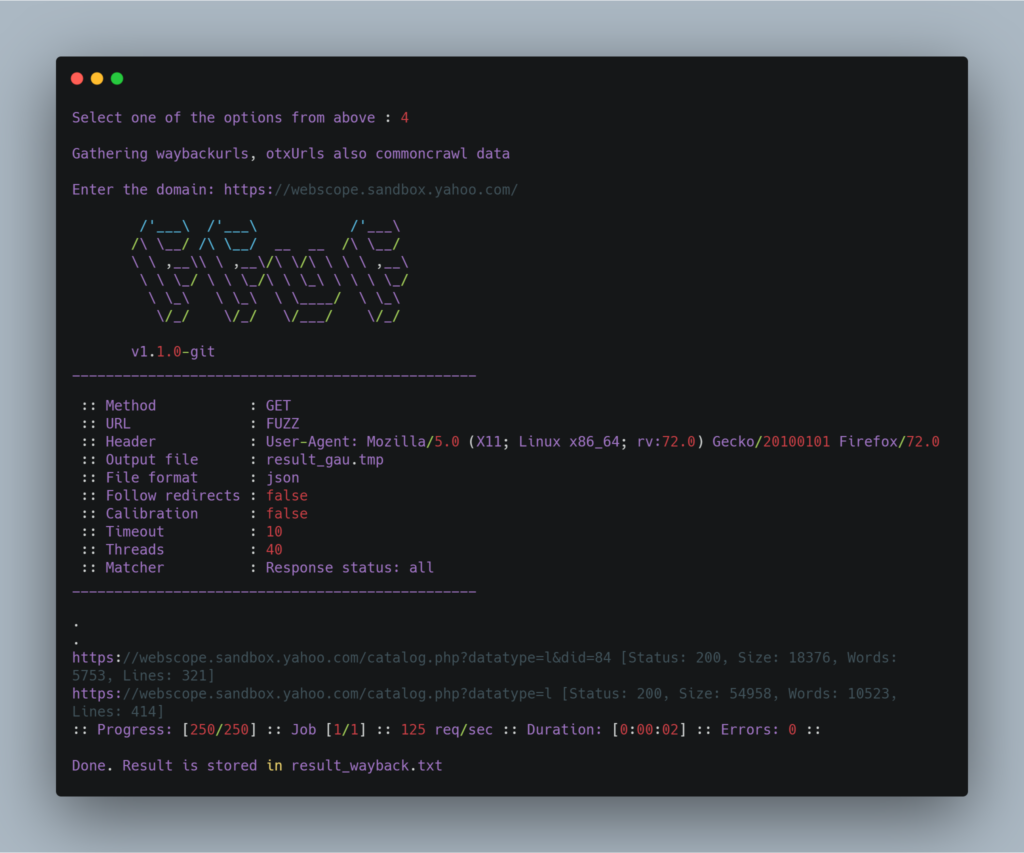
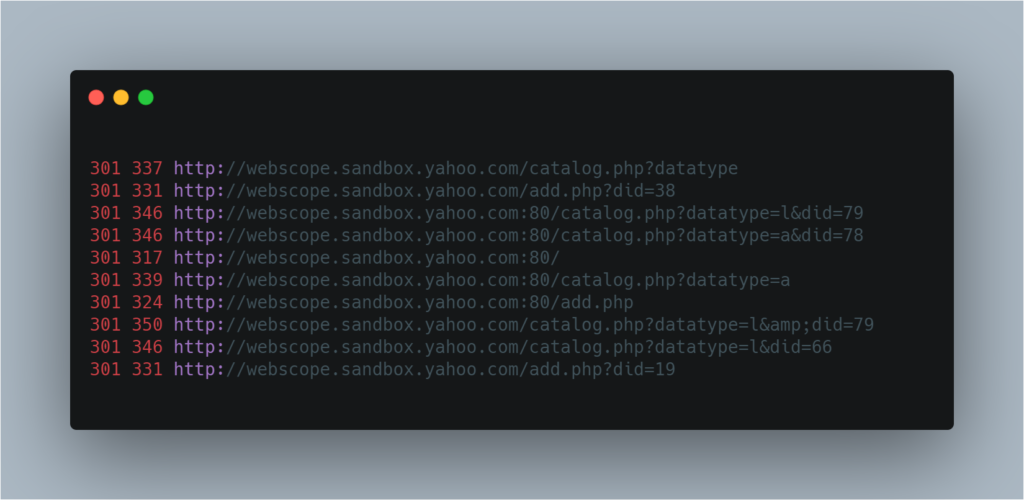
And will give the store the result in following format. You can easily review this result and look for inconsistencies very easily.
Coming to the Beast mode. This is insanely I have use xargs to launch 10 parallel instances of ffuf and used something called parameter expansion to store the results separately for each instance. I spent a week or something to come up with this complex one-liner and also had to ask around stack overflow to get things done. This one is awesome. And please run this on VPS if you don’t want to break your internet.
To use this mode, you have to put all the urls in alive.txt
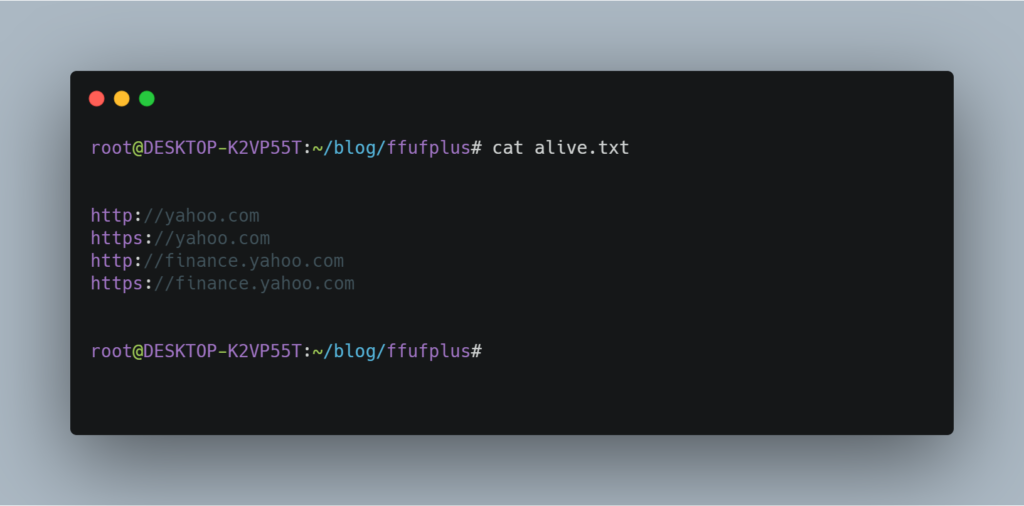
and then run this module
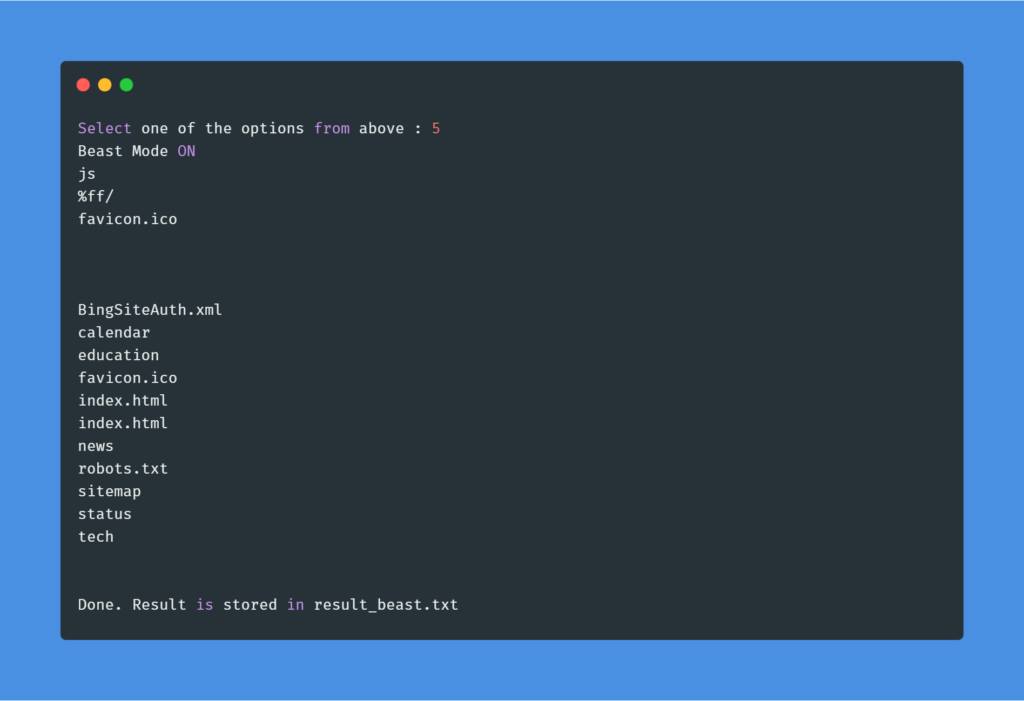
and the output result will be in this simple format.
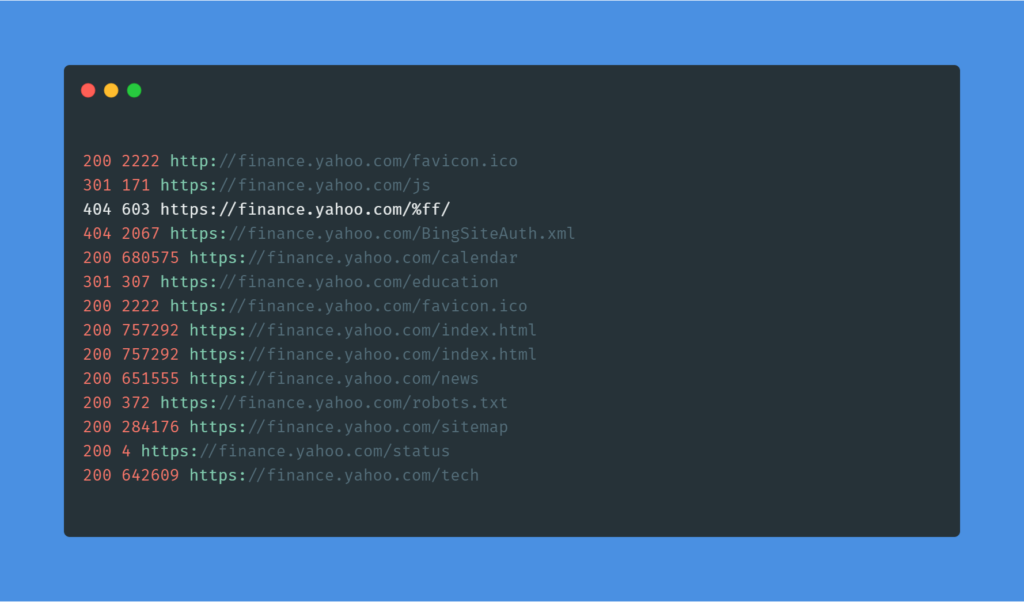
You can easily implement this one liner in you recon workflow and I am sure this will save you a ton of time.
Here is the link to my GitHub repository https://github.com/dark-warlord14/ffufplus . You can easily access the tool and download it. I also added an install script which you can use to install a few things before you run the tool. You can find other instructions in the GitHub repo.
I hope it helps you in some way. Feel free to connect with me on twitter @dark_warlord14 if you get stuck somewhere. Also please read my other writeup about Scanning JS files for Endpoints and Secrets.
Till then Happy Hacking!!
One Reply to “ffuf on Steroids”
Comments are closed.